BYOK; a false sense of security
Enterprises are moving IT workloads and functions to the cloud, usually without any strategies to secure sensitive data. The advantages of cloud computing, such as scalability, agility, and consumption-based pricing, are compelling enough to overlook the need of high level security.
while choosing a cloud service provider (CSP), security is rarely the first consideration. but after a few infamous cloud security breaches, CSPs have realized the increasing need for data protection and have started to offer new capabilities in this space.
One such capability cloud has introduced is Bring your own key- BYOK, but does it really contribute in meeting its increased security claim? let’s dig deeper.
Bring your own key
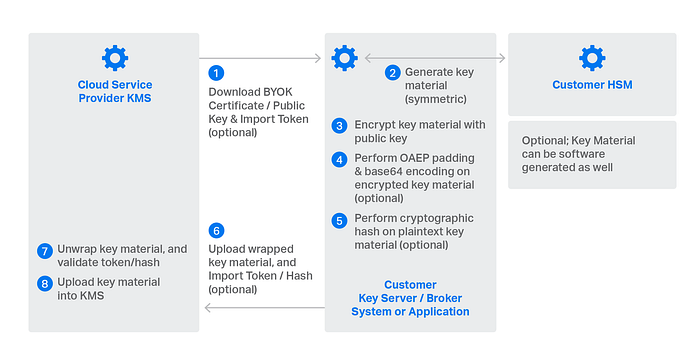
Organizations concerned about a CSP controlling the encryption keys of their data are told they can ‘bring their own keys’. CSPs allow customers to import their own key material. This model lets customers generate the keys themselves and upload them to the CSP’s key management system (KMS). Customers are required to download a certificate from the CSP, along with an import token.
The symmetric keys generated by the customer are encrypted using the public key of the downloaded certificate. The encrypted symmetric keys and the CSP token or a hash of the key material are then uploaded to the CSP KMS. The tokens/hashes are for authentication and integrity purposes.
Does it really gives the freedom it claims?
Although customer provides the key material, but CSP still owns or manages the master keys, which can be subject to any form of disclosure or abuse.
BYOK has created a false perception that customer ownership and control of keys is established when the fact is that, even if a customer generates and imports the keys into a CSPs key management system, direct or indirect control of the keys is in hands of the CSP.
BYOK is applied at varying tiers of the key hierarchy across CSPs, and customers are not necessarily in control of the keys that actually protect data.
like one CSP offers BYOK only at the fourth tier of its hierarchy, meaning that the other three keys; the second-level key encryption key (KEK), the first-level KEK, and the Data encryption key (DEK), all are owned by the CSP.
DEK ← KEK1 ← KEK2… ← KEKn (Your Key)
So regardless of the hierarchical tier where BYOK is offered to enterprises, CSPs have control over all keys present below. The perception created by CSPs is that the option of bringing encryption keys will provide organizations control and exclusive access to keys, when in fact it does not.
